The success or failure of your business hinges on your ability to understand and manage your risk tolerance. How much risk are you comfortable with? Should you play it safe and prioritize prevention, or swing for the fences and take the risk?
Every business is unique, so it’s a hard question to answer. A risk and control matrix (RACM) can help you analyze your risk profile and make better business decisions, faster. Let’s dig into what they are and how to use them.
What Is a Risk and Control Matrix (RACM)?
A Risk and Control Matrix (RACM) is a powerful tool that measures the potential risks you face against the control measures in place to mitigate their impact. Common risk types include financial, operational, IT, fraud, regulatory, or reputational risk. The matrix typically has two axes:
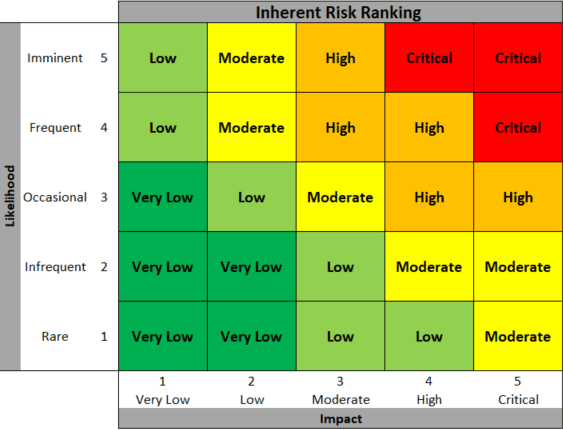
- Likelihood (or probability): This rates how likely a particular risk is to occur. It could be ranked from “rare” to “imminent.”
- Impact (or severity): This rates how severe the consequences would be if the risk actually occurred. It could be ranked from “very low” to “critical”.
Plotting these two factors for each risk helps prioritize which risks need the most attention, measure if the current controls are enough, and identify if additional measures are needed. It’s a great tool for better decision-making and communication around risk management.
Building Blocks of a RACM: Identify and Assess Your Risks
Imagine a data breach exposing your most sensitive customer information. The impact could be devastating for your business and its reputation, right? A well-defined RACM helps avoid that nightmare, preventing costly disruptions and safeguarding valuable information.
Not all risks affect organizations equally, so identifying and documenting each risk-control pair is crucial to understand the true impact. Before assessing risks, organizations need a clear understanding of three key concepts:
- Risk itself
- The difference between inherent and residual risk
- The criteria used for ranking each
What is risk?
Risk is defined by the Committee of Sponsoring Organizations of the Treadway Commission (COSO) as “the possibility that events will occur and affect the achievement of strategy and business objectives.” In simpler terms, risk is the potential for negative events to impact your organization’s ability to achieve its goals.
Inherent vs. Residual Risk
Within a RACM, each risk has both an inherent and residual risk ranking. Inherent risk is the raw, unaddressed threat before any controls, while residual risk is how much threat remains after you try to mitigate it.
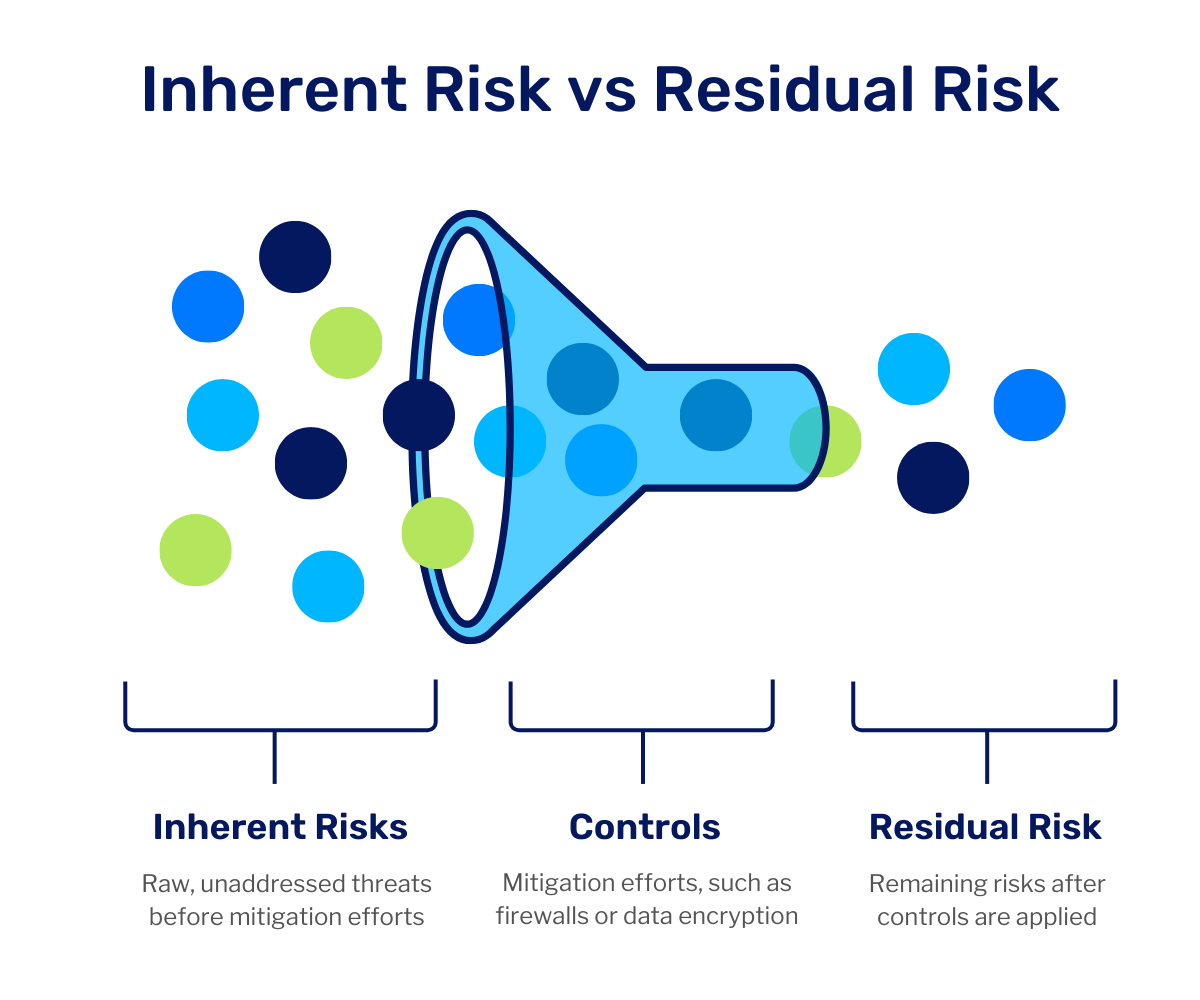
Inherent risk represents the baseline level of threat an organization faces before any controls are implemented. Imagine a power outage—the likelihood of it happening might be relatively low, but the impact could be significant. Assessing inherent risk involves evaluating both the likelihood and potential impact of a risk event occurring without any mitigating measures in place.
Residual risk reflects the level of risk that remains after controls have been implemented. These controls can be preventive (like strong passwords to prevent cyberattacks) or detective (like regular inventory audits to identify potential theft). Using the above example, the residual risk would be the remaining chance of a power outage occurring after implementing controls such as a universal power supply or battery backups to address the risk of an outage occurring.
Ideally, well-designed controls significantly reduce inherent risk, resulting in a lower level of residual risk. These valuable insights can help prioritize threats with the highest inherent risk or the most significant residual risk after controls and allocate resources properly.
Criteria for Ranking Inherent and Residual Risk
Assigning a clear ranking to both inherent and residual risk allows organizations to prioritize and allocate resources strategically. Here’s what organizations need to consider when establishing ranking criteria:
- Likelihood: This factor assesses the probability of a risk event occurring based on factors such as historical data, industry trends, or vulnerability assessments. For example, a cyberattack targeting a specific software program might be considered “medium” likelihood if there have been recent exploits, but “low” likelihood if the software is rarely used and well-patched.
- Impact: This assesses the potential consequences of a risk event, such as potential financial losses, operational disruptions, reputational damage, or legal implications. A data breach exposing customer information could have a “high” impact, while a minor power outage might have a “low” impact.
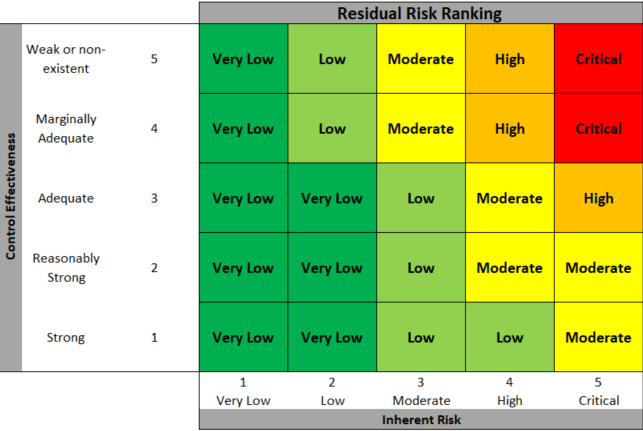
- Control Strength (Residual Risk Only): When evaluating residual risk, consider the effectiveness of existing controls in mitigating the inherent risk. This could be ranked as “weak,” “moderate,” or “strong” based on the control’s design, implementation, and ongoing monitoring. For example, a strong password policy and multi-factor authentication significantly reduce the risk of unauthorized access compared to a weak password alone.
By combining these factors, organizations can assign an overall risk ranking (often numerical or on a combined scale) to both inherent and residual risk to identify the most critical threats.
Considerations for Building and Updating Your RACM
The success of your RACM depends on keeping it complete, accurate, and current. Here are some key considerations to ensure your RACM is effective:
- Ensure a complete inventory of risks and controls: Are the risks and controls identified comprehensive enough to address your organization’s unique risk landscape?
- Align with processes and procedures: Do the risks and controls documented in the RACM reflect your actual financial, business, and IT processes as well as your organizational and departmental policies?
- Conduct periodic reviews: Establish a regular review process to assess risk rankings and criteria, evaluate opportunities to consolidate risks and controls, and ensure those responsible for maintaining the RACM confirm its accuracy.
- Back your decisions with documentation: Your RACM should be backed up by supporting workpapers that explain how you reached the conclusions in the matrix for transparency and traceability.
- Use the RACM to drive test procedures: RACM rankings should determine what needs to be tested. Higher inherent risks will require more rigorous testing procedures to ensure the effectiveness of the controls.
By addressing these considerations, you can ensure your RACM serves as a valuable starting point when approaching risk management and audit procedures.
Benefits of a RACM for Your Organization
Think of a RACM as a comprehensive roadmap guiding you through the risk management process, helping identify, assess, and ultimately manage risk exposure. It serves several key purposes:
- Prepare for audits and assessments like SOX compliance audits, internal audits, or cybersecurity assessments.
- Prioritize risks effectively and focus your efforts on the areas with the highest potential impact.
- Define and document control measures, including both preventive (like strong passwords) and detective (like regular inventory audits) controls.
- Evaluate control effectiveness, identifying areas for improvement or implementing additional controls where necessary.
- Minimize disruptions and safeguard assets by identifying risks early, minimizing operational disruptions and safeguarding valuable information.
Documenting the full environment of risks within a RACM is more than creating a list. It’s a valuable opportunity to identify potential gaps in your current risk management strategy and ensure your organization has a plan to mitigate risks that it’s not prepared to accept.
What to Do When Risk Management Feels Impossible to Manage
At SC&H, we believe in the power of proactive risk management. But when your team’s resources are stretched thin, it’s hard to be proactive.
Leveraging an experienced risk management partner can make the difference between success and catastrophe in a high-risk business environment. We go beyond simply building a RACM, working closely with your team to develop a comprehensive strategy tailored to your unique needs. This allows us to:
- Identify and address gaps in your current risk management strategy.
- Develop and implement effective controls to mitigate identified risks.
- Continuously monitor and improve your risk management processes.
Protect your business without wasting precious time or resources. Contact SC&H today to discuss how our process and strategy assessment empower your organization to navigate challenges with confidence and achieve long-term success.





